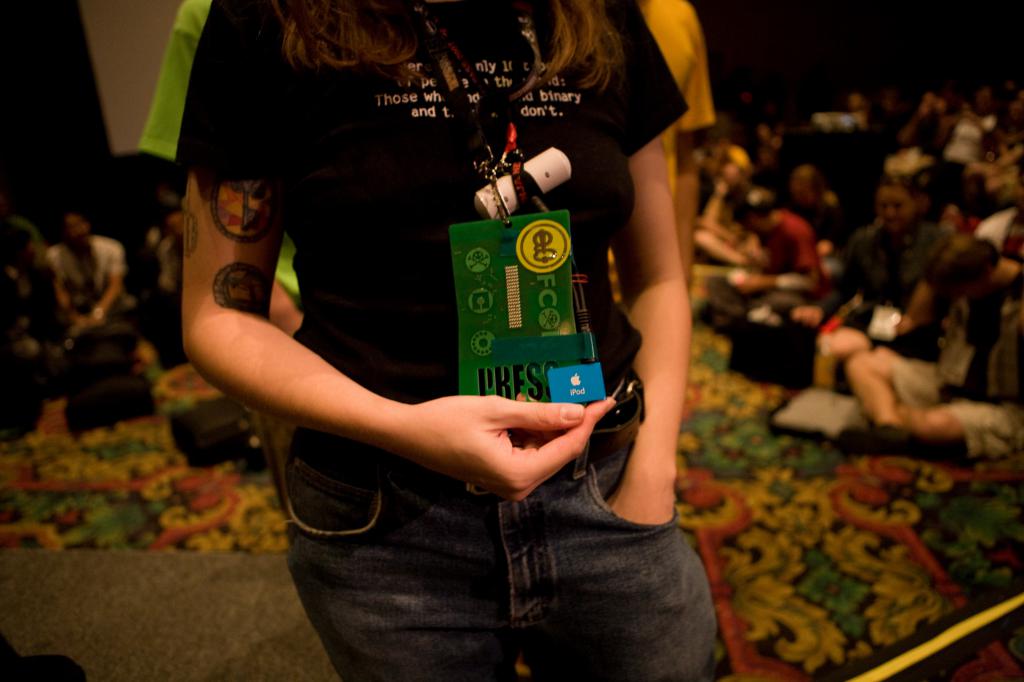I missed Claudio Merloni and Luca Carettoni's talk about their cool suitcase based bluetooth hacking system named BlueBag, because I was fighting an epic battle with a cruel hangover this morning. I did get a chance to talk to them and photograph the bag up close in the press room. The system inside is a low powered Micro-ATX motherboard running Gentoo Linux and the custom software that does the actual hacking will be available soon on their website. The system can detect and attack bluetooth devices from distances of over several hundred feet thanks to the built in amplifiers and the attacker can access the BlueBag system via a laptop remotely. The BlueBag has a side effect of knocking out 802.11b within about 10 meters due to the bluetooth amps. They chose not to fly with the BlueBag and instead shipped it in to Vegas, which was probably a good idea due to the extremely suspicious contents of the case. More photos of the BlueBag here.
Thursday, August 3rd, 2006 -
Read more...
yay that was fun!
check it out here
i wonder how long before it's in the tree?
Wednesday, November 6th, 2002 -
Read more...
So I finally got around to setting up cacti/snmp on my servers. Here is what I did:
- Installed cacti on the main monitoring server which we'll call slappy. I used the FreeBSD port of cacti. Slappy already had php/mysql/apache installed.
- Added a user snmp to slappy and then I generated keys using ssh-keygen for each of the servers that slappy would be monitoring.
- On each of the servers that slappy would be monitoring I installed net-snmp from the ports tree and configured it to run over tcp on 127.0.0.1 and then I added a user snmp with a nologin shell and without password authentication as I will just be using snmp to create a tunnel to the snmpd process that will be running on localhost.
- Back on slappy I su'ed to the snmp user and created a shell script that would set up the tunnels to each of the servers using a command like this:
ssh -i ~/.ssh/keys/hostname -f -N -L 16101:127.0.0.1:161 hostname and then added the script as a cronjob.
- Finally I added all the servers to cacti using the basic built-in net-snmp support as well as a couple of qmail and mysql scripts.
So I now have a nice collection of graphs for traffic / disk space / processor, memory and mysql load.
Saturday, November 26th, 2005 -
Read more...
As I mentioned in my previous blog posts, I attended my 6th Defcon this year. I had a great time and actually ended up getting hired by Wired Blog to shoot photos of the event, many of which can be found here. A few of them also made it onto the main Wired website. Of course I took hundreds of photos and only a handful were used by Wired, so here are some highlights from my collection:

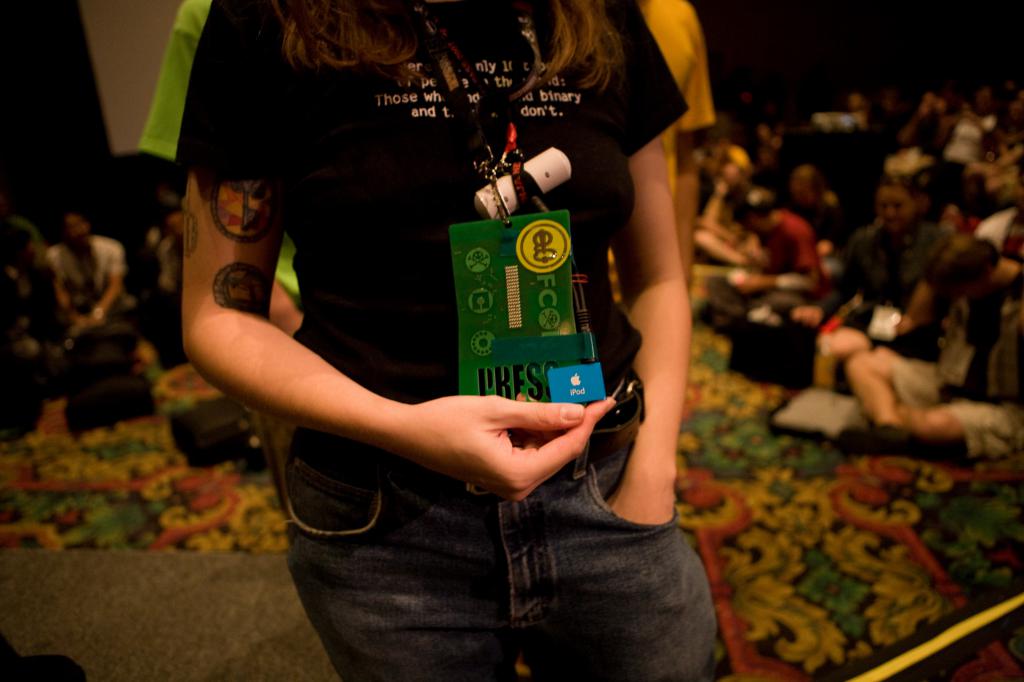



More after the jump, and the whole archive can be found in my Defcon 15 gallery.
Friday, August 31st, 2007 -
Read more...

I just caught the opening intro from Jeff Moss aka Dark Tangent. He dispelled rumors that Microsoft had attempted to buy a track at the convention, explaining that he was hoping to have some of the Vista engineers at the con to talk about their work that would hopefully coincide with the imminent release of the new OS. As it turned out the Vista release date has been pushed back, so that didn't work out as planned.
The opening keynote was given by Dan Larkin, FBIU Unit Chief of Cyber Initiative & Resource Fusion Unit Cirf-U, a spinoff of IC3. He started out with some bad jokes about how far computers have come which elicited a sum total of zero laughs from the audience. His talk became more interesting when he talked about strides the feds had made in past years working with academia, industry and experts in the field. The FBI is actively investigating all types of cybercrime ranging from phishing to spamming to bank fraud and are uncovering vast organized crime organizations that span the globe.
I had a chance to talk to Dan Larkin more after his talk and I asked him about what percentage of the crime the investigate involves music, movie and software piracy and he said that the organized criminals involved really have their hands in anything and everything illegal that can make them money. He said 30% of the bad guys crime involves When it comes to music, software and music.
I am torn between three of the next talks scheduled, of which I will try and catch a few minutes of each: Bypassing NAC by Ofir Arkin, Black Ops 2006 by Dan Kaminsky and Trusted Computing Revolution by Bruce Potter. Dan's talks are always great and I've enjoyed Ofir's in the past as well. I am pulling the shots from the keynote off my CF card right now and will upload them as soon as they are done.

Wednesday, August 2nd, 2006 -
Read more...

Frequently you find a speaker who is covering a very interesting topic, but may not quite have a firm grasp on keeping a crowd interested. Public speaking is not a skill that I have mastered, and I feel that the folks that were talking about Sidewinder are in the same boat. Sidewinder is a promising piece of software that Shawn Embleton, Sherri Sparks and Ryan Cunningham are working on. Sidewinder is a fuzzer that uses genetic algorithms to evolve the fuzzed input in order to get the funky data to the place in the code where you want it. The next logical step of their application is to add some software to create exploits once you get to the place in the code where you suspect a vulnerability may exist. Keep an eye on these three, I see big things coming from their collective intelligence in the next few years.
Update I had a chance to speak with Shawn about the Sidewinder application and he told me it was all coded in just a few months. He isn't sure if he will have time to continue development on the application, but I encouraged him to as I feel it is a great concept and could grow to be one of the best fuzzers out there.
Wednesday, August 2nd, 2006 -
Read more...
I wrote an article a few months ago about using freebsd and ipfilter to do transparent bridging in combination with ipfw. This article goes into further detail about monitoring the firewall.
In my previous article I talked about zeebeede. I've decided against using at as I found that net-snmp now allows for the daemon to bind to tcp instead of udp. This makes it easy to set up an ssh tunnel which will give us a secure means of transfering the snmp queries over the wire...
Monday, December 9th, 2002 -
Read more...
I have arrived in Las Vegas for Defcon and Black Hat (not in that order). I love Defcon. I believe this will be my 8th year at the 'con. I've been covering it for Wired since last year and for my own blog the year before.
I also posted a sneak peek of the Defcon 16 badge on Wired.com earlier this week. I can't wait to get my hands on a production version.

A nice selection of supplies covers my bed including 8 SD cards (for friends), IR LEDs, a soldering station, a bare bones arduino, a breadboard, various components and Maker's Mark.
Thursday, August 7th, 2008 -
Read more...
According to experts at a computer conference in Brasilia, the world's "hacking capital" is in Brazil... does this have anything to do with Terry Gilliam? haha [bbc world]
Wednesday, September 15th, 2004 -
Read more...
Not that they are going to guess any of my passwords with this scanning (as I use difficult, non english, symbol filled passwords) but it still pisses me off:
Saturday, September 10th, 2005 -
Read more...

I am attending a 2 day security convention in Las Vegas called Black Hat. The flight in from LAX was short, although I did get the old TSA hassle, for the first time ever I was directed to stand in the little search corral and the frisked me, then swapped my bags and fed that to the spectrometer, I heard from another attendee that people all over the country are getting extra hassles.
I showed up at Caesar's Palace right at 8am to get my credentials and everything went smoothly. The line for the general credentials was insanely long, but luckily there was a press line that was only a dozen or so people deep. Jeff Moss will be giving his intro in a few minutes and then the keynote: "Fighting Organized Cyber Crime", which should be interesting. I'll get some photos of the speakers and try and upload them and give an update between talks. The photo above is of the free swag you get upon registration... a pretty good haul.
Wednesday, August 2nd, 2006 -
Read more...

I just got my wife's badge for Defcon (they're not giving out press badges 'till tomorrow) and it is totally and completely awesome. At first when I put the batteries in, the LEDs lit up and then nothing happened. I tried shorting a few pins together on the back to no avail and then by accident I figured out that the front has two buttons, which are the smiley skull and the dial. After pressing the buttons it scrolled some text about Defcon, and then I hit the buttons a few more times and saw POV, which stands for persistence of vision. I swung the badge around and saw the word defcon, just like the cool spoke POV kits. Then I pushed the buttons a few more times and it displayed: TEXT. I held both buttons at once and I was able to program in 15 characters of text using the buttons to navigate and pressing them both at once to select a letter. I choose: "EECUE[HEART]PENELOPER^" with the heart being an actual heart symbol. The badge offers a full upper and lowercase alphabet along with an assortment of symbols and punctuation. After adding the 15 characters the text began to scroll in a marquee fashion. This is the dopest badge ever. Hell yeah and way to go Defcon!
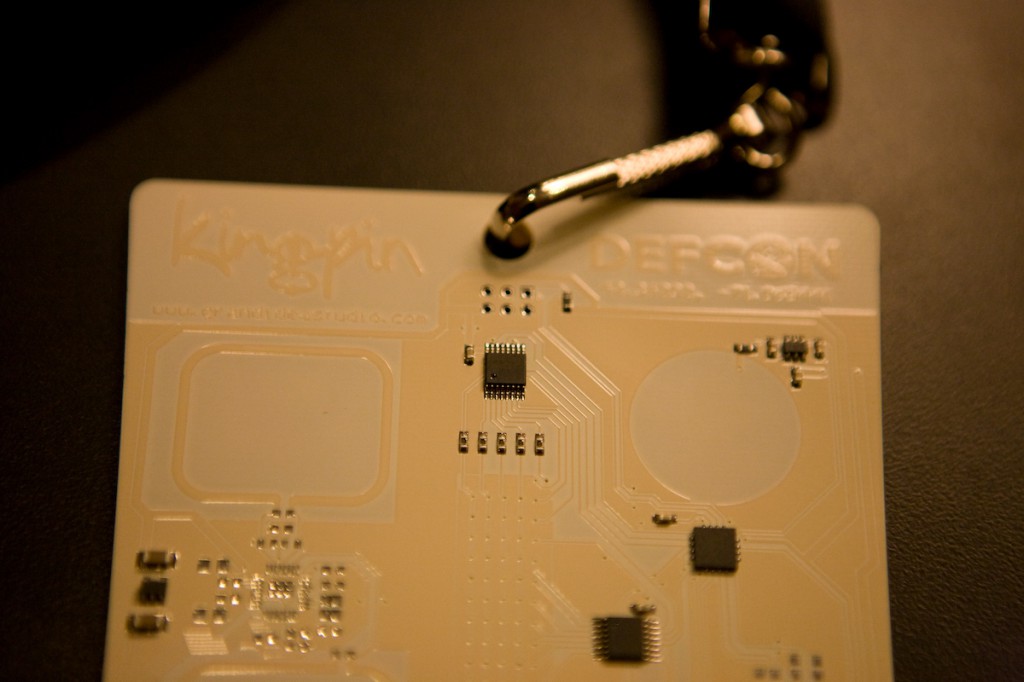
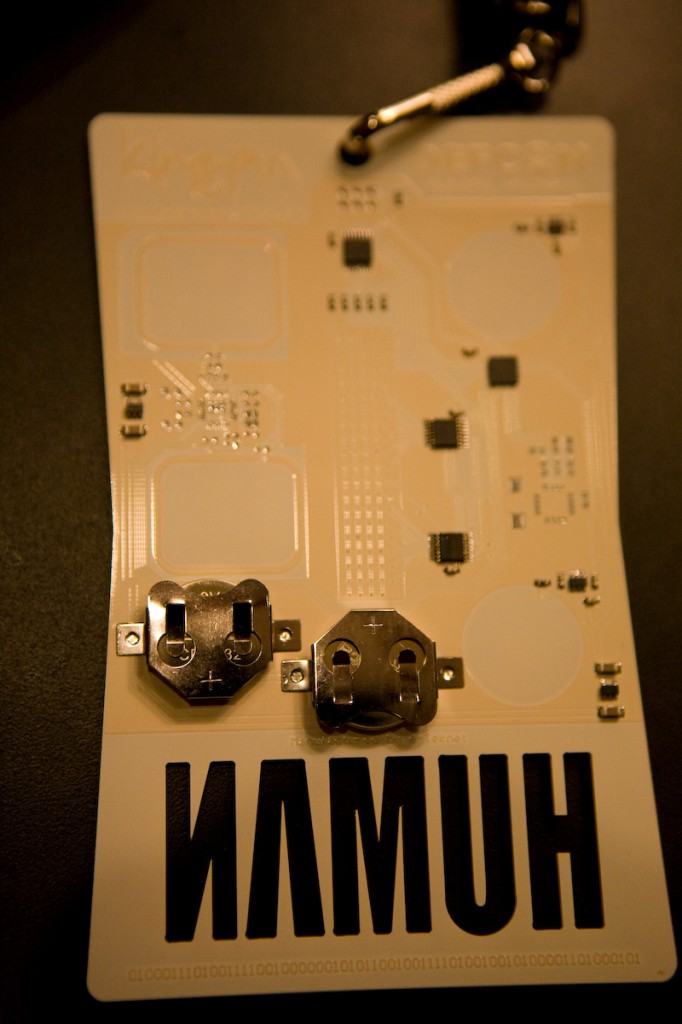
Thursday, August 2nd, 2007 -
Read more...

"Faster Pwning Assured: Hardware Hacks and Cracks with FPGAs" with David Hulton & Dan Moniz. I didn't stay for this talk, as I'd seen Hikari's original talk at LayerOne a couple years back, but I did get a couple shots of him and the expanded setup of FPGAs.

Thursday, August 3rd, 2006 -
Read more...
Photos and words coming soon.
UPDATE!
So believe it or not I have been slammed at work since I got back from the con and I really haven't had any time to sort my photos and write about my experiences at DEFCON, or at the parties I attended. I just got back from the walking tour of Downtown LA focusing on the Art Deco buildings in the area. I took some photos and I'm going to both sort those and the DEFCON pics and upload tonight.... oh and another thing... if I have time tomorrow I will be releasing a few more pages of LA from an Auto.
UPDATE 2
Oh my it must be a chilly day in hell as Penelope posted two entries on her site!!! One is a review of defcon... good job sweetie!
Monday, August 1st, 2005 -
Read more...
Last weekend I covered Defcon 16, the world's largest hacker convention for Wired.com's Threat Level blog. Like last year, I was paired with Kim Zetter, one of Wired's best writers and an all around cool person.
Zetter wrote all the serious articles, which I provided pictures for. These articles included:
I did end up writing a few features that weren't hard news, but were still fun to write and shoot:
The Defcon NOC piece ended up on the front page of Slashdot, Gizmodo, Hack A Day, BoingBoing and more. Some of the other pieces I wrote also got picked up on various other sites.
I had a great time this year at Defcon, it was my 8th Defcon and I can't wait for next year. I'm looking forward to working with Zetter again and getting another tour of the NOC!

Wired.com piece in which I toured the Defcon Network Operations Center.
Tuesday, August 12th, 2008 -
Read more...
The guys from a wireless research company called Flexilis who happen to be based a block and a half from my loft, just showed me their proof of concept demo of a serious flaw in the upcoming RFID embedded Passports, scheduled to be released in October. The RFID passports incorporate a shielding mechanism to prevent rogue readers from picking up the sensitive information contained in your US passport, but as it turns out if the passport is slightly open it can be read. This may not seem like much of a big deal until you watch the following video where they created a proof of concept Improvised Explosive Device that detects the presence of a US passport and detonates a charge (or in their test case, some model rocket engines).
This hack could also be used to identify to unique individual and then detonate a device or track them. Because the RFID technology works at only close distances this attack is especially dangerous. I talked to them about the possibilities of attacking the RFID chip even if the passport is closed and it is possibly that with a very strong electromagnetic field, the data could be read on a subcarrier, but they still have more research to do in that area. Here is their abstract about the demo:
The FLX[2006‐0605] video security brief demonstrates a real‐world
vulnerability associated with the failure of the shielding component in the current
proposed electronic passport design. When partially open, as could be the case when in a
pocket, purse, or briefcase, the currently proposed passport can be detected by a nearby
inquiring RFID reader. The security brief also demonstrates an improved shield design
that requires a passport to be significantly open before reading is possible.
You can read the full RFID Passport Technical Analysis (84K PDF) or the RFID Passport Shield Failure Demonstration (120 KB). The good news is they have proposed a fix for the problem, John Hering told me he had discovered the vulnerability 2 years ago, but didn't want to release knowledge of the problem until he had a fix to go with it.
Digg This Article
UPDATE Well it looks like the Department of State decided not to wait until October to begin issuing these dangerous passports. Here is their press release.
Wednesday, August 2nd, 2006 -
Read more...
Once a year hackers, crackers, geaks, freaks, drunks and gun toting maniacs get together in Las Vegas for the security convention known as DEFCON. Although the con has many speakers and events in the past I have gone to eat, drink and be merry in LV and this year will be no exception as thoughts of Nobu, Bellagio Buffet and Habeñero Rum dance through my head. 23b.org (which I host / am a member of) is a great spot to find photos from the con both past and present. If you're going, I'll see you there!
Tuesday, July 26th, 2005 -
Read more...
Now that money is involved it will only be a short amount of time before RFIDs are blown wide open as the next huge security problem. All you have to do is excite the card with the right radio freqs and pick up the response and you're in. Record it, replay it and you have pwn3d the money.
Tuesday, November 8th, 2005 -
Read more...
Thank you Comcast for lowering the amount of spam in the world by blocking port 25 on your periphery. When the clusestick whacking fails, block port 25.
Friday, July 2nd, 2004 -
Read more...
This Saturday at 12:30pm I will be available for dunking in the DefCon EFF dunk tank. The proceeds go to the EFF so it is for a great cause. You know you want to dunk me!
Tuesday, August 1st, 2006 -
Read more...
The feds have some crazy idea in their minds that making a gigantic database of everyones information is a good idea. It's not. The feds can't even secure there own computers let alone a system with everybody's info on it... did i mention a convicted felon will be heading this project?
Thursday, December 5th, 2002 -
Read more...
For the last three years we have brought you panels of security experts from
some of the members of the most elite hacker groups in Southern California.
This year we present the Orange County Hacking Summit IV - No Protection
version 2.003. This year we will be presenting some of the best and
brightest security engineers and hackers of the So Cal hacking and computer
underground community.
Friday, May 2nd, 2003 -
Read more...
You can open Kryptonite locks using a bic pen. [meme pool]
Wednesday, September 15th, 2004 -
Read more...
The self contained, easy to set up Cobalt RAQ server appliance now maintained by Sun Microsystems is vulnerable to a remote root exploit which ironically affects the SHP (security hardening package). Grazer released the advisory along with an exploit on i-security.nl. A patch for the problem is available for download.
Thursday, December 5th, 2002 -
Read more...

As everyone in attendance should know, the Defcon network is probably the most dangerous and hostile network in the world. No network is secure, but the wireless network at Defcon is totally insecure with thousands of hackers and script kiddies sniffing traffic and actively attacking ever system they see. This is one reason why I've made it a habit to use an out of band connection for my internet needs. My out of band network of choice is EVDO, but even with that I still send all my traffic through an ssh tunnel to a trusted host.
Verizon's EVDO uses ppp to assign you system a public internet address, and I'm guessing that the IP range varies from city to city. It's no surprise that people know about this as evidenced by the logs below that show port scans bouncing off my firewall.
One of the talks coming up today is "Hacking EVDO," and I was a bit worried that someone had figured out how to sniff EVDO traffic. I happened to run in to King Tuna, who is giving the talk and asked him about what he had found. He told me that currently the protocol is still secure, but that he had found a vulnerability in one of the chipsets which he has written an exploit for. The point of his research was to inspire other people to work on the protocol and break it.
The logs from my firewall can be found after the jump.
Saturday, August 4th, 2007 -
Read more...

Yesterday at Defcon I went to the vendor area to pick up the Zigbee and accelerometer chips for my awesome Defcon badge. Unfortunately they were out of both chips, but they did let me borrow their soldering iron and gave me some leads to solder onto my badge. I soldered these leads on in a minute or two and then attached my badge to their laptop which had the freescale programming software on it. I modified the source code, which is actually in C, simply changing the hard coded message from "I <3 DEFCON" to "eecue.com." Changing this, meant that as soon as I powered up the badge it displayed that instead of the default message, and also changed the POV message. After modifying the code, I recompiled the firmware and flashed it to the badge.

The hack was simple and in total took me about 10 minutes. According to the guys at the booth and Joe Grand (the badge's designer) I was the first person at the con to hack a badge. Today I am planning on picking up my own Freescale programmer and the accelerometer chips which should be in stock, and hopefully I'll find some time to modify the badge in more interesting ways. This simple hack has been written up on Wired's 27bstroke6 blog (whom I have been employed by for the duration of the convention as their staff photog), Gizmodo and several other places.

Saturday, August 4th, 2007 -
Read more...
This weekend in Las Vegas, the world's largest hacker convention, DEFCON, will be taking place. As opposed to what the register says, there will mostly be drinking and more drinking.
[the register uk]
Monday, July 26th, 2004 -
Read more...
Ok so i hacked up nat so that it would compile on jaguar (os x 10.2) and i have it available for download here
i want to add it to the fink tree but i'm not sure where to start... the online docs didn't help me during the 10 mintues i looked at them... for now you can grab it off my site here. but
somday i'll figure out the right way to put it in fink...
Wednesday, November 6th, 2002 -
Read more...
This is the craziest email scam I've ever gotten. It would be totally plausible if there was any chance that Benazir Bhutto whould have had my email address in her address book. I almost want to respond to see what kind of a scam it is, but I'm sure it's just your average Nigerian Email scam:
From: XXXXXXXXXXXXX@yahoo.com
Subject: Re: Benazir Bhutto
Date: March 31, 2008 10:28:38AMPDT
To: undisclosed-recipients: ;
Hello,
I want to take this opportunity to express my heartfelt appreciation to
you for your support during the hour of need. The enemy gave us a huge
blow when they took the life of my dear mother. As a matter of fact, I do
not know you personally except your contact details I got from my mom's
address book. I also pass on my sincere appreciation for the feat we were
able to record at the last elections despite the absence of my mom who was
the party leader until her brutal assassination. The victory was to all
Pakistanis as it clearly demonstrated their commitment to the course my
mom stood and died for. Your support is conspicuously recognized and
highly appreciated.
Losing her is the hardest thing I've been through all my life, but knowing
that she was a hero to many people does comfort me. I know she would
appreciate what you all did for her. All we just crave for now is for her
killing be probed by an international team under the United Nations. It is
the only hope we have of getting the possible plotters of her murder
properly investigated. Only this would help us convince our supporters
that there was some element of collusion between her murderers and agents
of President Musharaf who were determined to get rid of her.
Please do acknowledge receipt of this correspondence as I will be
confiding something very important in you when I get to hear from you
again.
Very sincerely,
Bilawal Zardari.
Monday, March 31st, 2008 -
Read more...
I no longer have a catch-all email address. For years the email (qmail) server that I run was set up to receive anything @eecue.com. So if you sent an email to asdflakhjflakjsf@eecue.com or daveisameanperson@eecue.com I would receive it. This was helpful as it allowed me to create addresses for every site that I submitted my information to, such as target@eecue.com, amazon@eecue.com, etc. That way if those companies sold my address to a list I would know they were responsible for the spam.
This seemed like a good idea until I started getting dictionary Joe Jobbed a few years ago. A Joe Job is when someone sends emails from your account to discredit you. In my case it was just a spam bot sending spams from random addresses @eecue.com. I don't think it was an attack on me, I just have a short domain name that has a catch-all address.
The joe-jobbing caused me to receive thousands of bounce messages. Today I finally decided to turn off the catch-all functionality in my email server. First I dug through my archived mail to find any important addresses that I still needed to receive mail at. I added aliases for the ones that would be hard to change. Any address that was easy to change I just logged into the site it corresponded to and changed it to my main address.
After getting rid of the catch-alls I set up a Sender Policy Framework (SPF) record on my DNS server. SPF is a record on a name server that tells mail servers which IP addresses are allowed to send email for that domain. Luckily I only ever send email from my personal mail server so that was easy to fix.
These changes should greatly reduce the amount of spam and joe-job bounces I receive.
Friday, May 30th, 2008 -
Read more...
ok so the defcon bbs is live for the next 12-24 hours (or until i get
to defcon). here is the url:
http://dc11.eecue.com/
read on ....
Thursday, July 31st, 2003 -
Read more...
This is priceless, the DHS has recommended that users switch to a browser other than Internet Explorer, due to serious security flaws. So i would recommend that you download and install Mozilla.
Friday, July 2nd, 2004 -
Read more...
People love free booze and tickets to parties at which free booze is provided are a hot commodity at security conventions. A company called Tipping Point that is a subsidiary of 3Com is throwing a party tonight at Body English in the Hard Rock. To get an invite you would have had to RSVP with their PR people before the convention, which of course I didn't, or you would have to wait in "line" and get a ticket on a first come first served basis. I put line in quotes because the folks manning the booth didn't seem to have any idea about how to do an orderly giveaway. They told everyone to stand there and wait their turn, but never actually instructed people to get into a single file line. The "line" was actually more like a mob and when they started giving away the tickets it turned into a writhing blob of stinky geeks, I almost lost my camera bag in the chaos. In the end I got my pass to the party and I will go and take part in the booze drinking. I don't want to make a presumption about the quality of their product based on the lack of organization of their giveaway, but it is hard not to.
Update Last night we defeated the authentication system of the Tipping Point party and got about 12 people in with just the 1 token I won, plus 2 or 3 tokens that we temporarily borrowed from random people. The flaw in the system was pretty simple, the bouncers didn't take your token away when you got in so if you went outside to make a phone call or whatnot you could give your token or several you borrowed to your friends. The part was fun and being 23b, we danced.
Wednesday, August 2nd, 2006 -
Read more...
link to the package
NetBIOS Auditing Tool Release
As of February 16th Secure Networks Inc. has released a free (GPL`d)
NetBIOS auditing tool for use both on WindowsNT and UNIX platforms.
The tool itself is designed to test NetBIOS file-sharing configurations as
well as Password integrity of remote stations.
The toolset is available via the following channels:
ftp://ftp.secnet.com/pub/tools/nat10/nat10bin.zip (For NT and Win 95 binaries)
ftp://ftp.secnet.com/pub/tools/nat10/nat10.tgz (For full source)
http://www.secnet.com/ntinfo/ntaudit.html A technical description of how the NetBIOS auditing tool works follows.
The NetBIOS Auditing Tool (NAT) is designed to explore the NETBIOS file-sharing
services offered by the target system. It implements a stepwise approach to
gather information and attempt to obtain file system-level access as though
it were a legitimate local client.
The major steps are as follows:
A UDP status query is sent to the target, which usually elicits a reply
containing the Netbios "computer name". This is needed to establish a session.
The reply also can contain other information such as the workgroup and account
names of the machine`s users. This part of the program needs root privilege to
listen for replies on UDP port 137, since the reply is usually sent back to UDP
port 137 even if the original query came from some different port.
TCP connections are made to the target`s Netbios port [139], and session
requests using the derived computer name are sent across. Various guesses at
the computer name are also used, in case the status query failed or returned
incomplete information. If all such attempts to establish a session fail,
the host is assumed invulnerable to NETBIOS attacks even if TCP port 139 was
reachable.
Provided a connection is established Netbios "protocol levels" are now
negotiated across the new connection. This establishes various modes and
capabilities the client and server can use with each other, such as password
encryption and if the server uses user-level or share-level Security. The
usable protocol level is deliberately limited to LANMAN version 2 in this
case, since that protocol is somewhat simpler and uses a smaller password
keyspace than NT.
If the server requires further session setup to establish credentials, various
defaults are attempted. Completely blank usernames and passwords are often
allowed to set up "guest" connections to a server; if this fails then guesses
are tried using fairly standard account names such as ADMINISTRATOR, and some
of the names returned from the status query. Extensive username/password
checking is NOT done at this point, since the aim is just to get the session
established, but it should be noted that if this phase is reached at all MANY
more guesses can be attempted and likely without the owner of the target
being immediately aware of it.
Once the session is fully set up, transactions are performed to collect more
information about the server including any file system "shares" it offers.
Attempts are then made to connect to all listed file system shares and some
potentially unlisted ones. If the server requires passwords for the shares,
defaults are attempted as described above for session setup. Any successful
connections are then explored for writeability and some well-known file-naming
problems [the ".." class of bugs].
If a NETBIOS session can be established at all via TCP port 139, the target is
declared "vulnerable" with the remaining question being to what extent.
Information is collected under the appropriate vulnerability at most of
these steps, since any point along the way be blocked by the Security
configurations of the target. Most Microsoft-OS based servers and Unix SAMBA
will yield computer names and share lists, but not allow actual file-sharing
connections without a valid username and/or password. A remote connection to
a share is therefore a possibly serious Security problem, and a connection
that allows WRITING to the share almost certainly so. Printer and other
"device" services offered by the server are currently ignored.
For more information about NAT see:
http://www.secnet.com/ntinfo/ntaudit.html - Oliver Friedrichs
---
Secure Networks Incorporated. Calgary, Alberta, Canada, (403) 262-9211
Tuesday, November 12th, 2002 -
Read more...
I forgot to mention it but a month or so ago I won the going postal quiz challenge... it was pretty straight forward and from it I gained access to the attrition.org photo gallery. I haven't used it yet, but someday it may come in useful.
Sunday, July 30th, 2006 -
Read more...
The DC11 media archives are now online... you can get real audio and video of all the talks you missed because you were too drunk to see them.
Monday, July 19th, 2004 -
Read more...
If you don't make it public, nobody will know you failed... well except the attackers who brought down your network.
Thursday, June 24th, 2004 -
Read more...