A few days after Christmas I received an email from an upset University server admin who thought my servers were attacking his servers through email. What was actually happening was that a spammer was sending email using random fake address at his server's domain name which I will call anonymous.edu. It wouldn't have been a problem if the server was correctly responding with 550 errors which mean Permanent Failure, but the servers were sending 450 which are Temporary errors, so all the servers that were trying to deliver the bounces, kept trying.
So here is the first email I received from postmaster@anonymous.edu:
From: [email protected]
Subject: Hosts from your domain are attacking our server
Date: December 28, 2004 2:19:23 PM PST
To: [a bunch of my email address]
Network/Security Administrator,
I'm sending you this mail because one or more IP addresses in your domain
are currently attacking our electronic mail server with a denial of service
attack consisting of multiple, rapid attempts to send mail to randomly
generated, non-existent email addresses.
Please take action with regard to the below hosts immediately to stop this
worm or virus. This attack may be reported to the U.S Federal Bureau of
Investigation for criminal prosecution. These hosts may also have been
blacklisted from sending mail to our server.
64.239.136.142 (www.eecue.com)
To which I responded:
From: eecue AT eecue.com
Subject: Re: Hosts from your domain are attacking our server
Date: December 28, 2004 2:32:16 PM PST
To: [email protected]
Hi you will notice those emails are not actually coming from my server.
The spammers are using my domain as their From: address.
Is this email for real?
-Dave
My guess was close, but I had it backwards...
After getting three more of those emails they sent me this:
From: [email protected]
Subject: Hosts from your domain are attacking our server
Date: December 28, 2004 2:59:32 PM PST
To: [a bunch of my email addresses]
Excuse me if this email is a duplicate. I forgot to list the IP address
of the victim of this attack. It is: atlantis.anonymous.net (192.168.139.69)
Also, I can be contacted at: [email protected]
I'm sending you this mail because one or more IP addresses in your domain
are currently participating in a distributed denial of service attack
consisting of multiple attempts to send mail to randomly generated,
non-existent email addresses at our site.
Please take action with regard to the below hosts immediately to stop this
worm or virus. These hosts may also have been blacklisted from sending
mail to our server. They can be re-enabled once the DDoS attack subsides.
64.239.136.142 (www.eecue.com)
To which I responded this:
From: eecue AT eecue.com
Subject: Re: Hosts from your domain are attacking our server
Date: December 28, 2004 3:01:28 PM PST
To: [email protected]
Hello,
Please send me the full email in question including the headers
so I can track down who is sending said email.
Thanks
-Dave
I didn't hear back about it until today when I received this email:
From: anon\[email protected]
Subject: Re: Hosts from your domain are attacking our server
Date: January 3, 2005 12:42:57 AM PST
To: eecue AT eecue.com
It was for real, but was the result of a mis-diagnosis of the problem...
Things have returned to normal, there is no need to do anything on your
side. Our domain was the subject of a massive spam forgery ("Joe Job")
with randomly generated reply-to fields @anonymous.edu. This occurred for over
14,000 domains, and our mail server was sending a 450 temporary error.
Basically we told 14,000 sites to keep trying to deliver bounce messages
back to us, with no valid local recipient, at whatever rate they did queue
flushes. Making it look very much to us like a Distributed Denial of
Service Attack. When really this whole thing would have been only briefly
painful if we had changed the failure notice to a permanent failure,
causing those 14000 servers to trash those invalid messages.
It was not apparent to us what was happening (since we never received any
of the bounces) until someone said, "Hey you know this bounce says that you
are replying with a 450 temporary failure..." It has now been changed to a
550 (permanent failure) response.
Thanks again for looking into this!
Well that was nice of them to fix everything.
From: eecue AT eecue.com
Subject: Re: Hosts from your domain are attacking our server
Date: January 3, 2005 7:17:39 PM PST
To: anon\[email protected]
Glad you worked everything out.
I thought it was somewhat humorous, so I posted about it on my website:
http://eecue.com/
I changed the names to protect the innocent.
-Dave
....
A. David Bullock
eecue : programmer / designer / admin / human
http://eecue.com/ -
anything is possible
Read more...


















































 Last night my friend Don Smith aka Don of the Desert died in a fire at his residence in Twentynine Palms. Don was a master welder and could fabricate anything imaginable out of metal. Rest in Peace Don.
Last night my friend Don Smith aka Don of the Desert died in a fire at his residence in Twentynine Palms. Don was a master welder and could fabricate anything imaginable out of metal. Rest in Peace Don.

































 You're technically not allowed to take photos at the
You're technically not allowed to take photos at the 














































































































































































































 Just got back from a snowshoeing / backpacking trip with my lovely fiance
Just got back from a snowshoeing / backpacking trip with my lovely fiance 

















































.jpg.jpg) This is a random picture of Steve Kemst that I took after respect. As you can see we are standing outside. I posted it instantly with my new photoblogging feature that i just programmed a few nights ago. Fun stuff.
This is a random picture of Steve Kemst that I took after respect. As you can see we are standing outside. I posted it instantly with my new photoblogging feature that i just programmed a few nights ago. Fun stuff.

























































.jpg.jpg) This is a random and pointless photo of some sauce at dinner
This is a random and pointless photo of some sauce at dinner








































































































































 A few years ago I got a tour of One Wilshire in Downtown Los Angeles where I took some cool pictures. Some of them were also at Pajo Networks which is now called Tier Zero. I host my servers with Tier Zero.
A few years ago I got a tour of One Wilshire in Downtown Los Angeles where I took some cool pictures. Some of them were also at Pajo Networks which is now called Tier Zero. I host my servers with Tier Zero. 










































































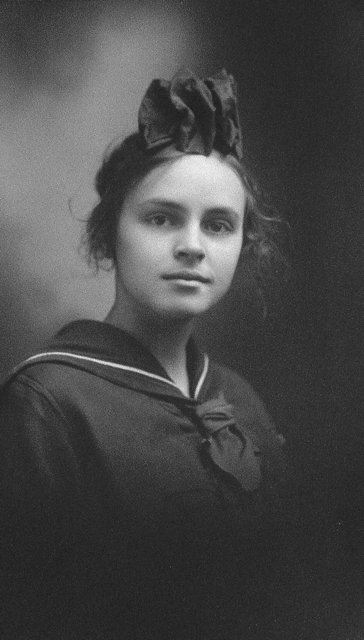

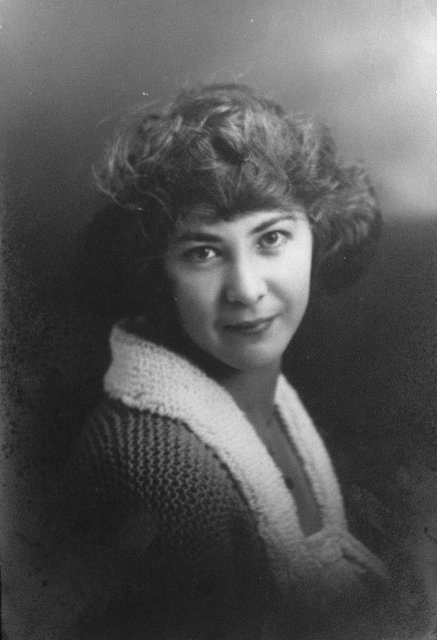






































































































































































































































































 As of November 24th, 2004 I am now engaged to the lovely and beautiful Penelope Proffitt. I love her very much and am looking forward to a wonderful life with her.
As of November 24th, 2004 I am now engaged to the lovely and beautiful Penelope Proffitt. I love her very much and am looking forward to a wonderful life with her.